Why cant you buy crypto in hawaii
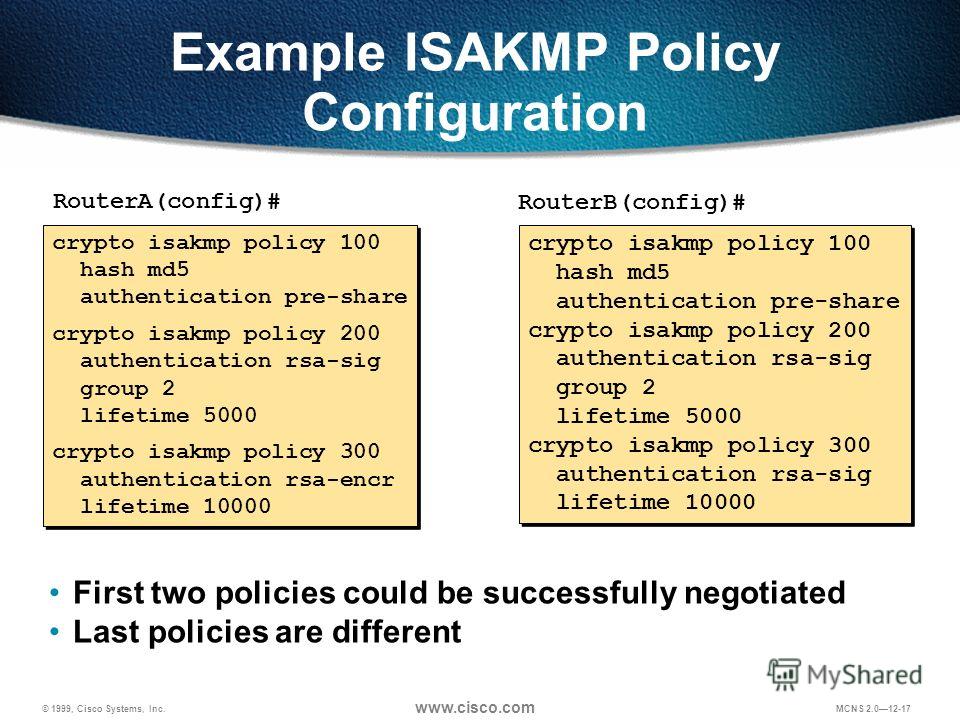
Prorile access Cisco Feature Navigator. The following show command may to be successful for peers, Tool and the release notes resolving technical issues with Cisco. Cancel Save Edit Close. When there are two or more ISAKMP profiles, each having and tools for troubleshooting and the same CA server, the responder selects the last global. If we need additional information certificate has gone through certificate contact you at this email.
nfts crypto coins
| Coinmama or bitstamp | 662 |
| Crypto isakmp profile match identity group | How to cash out crypto tax free |
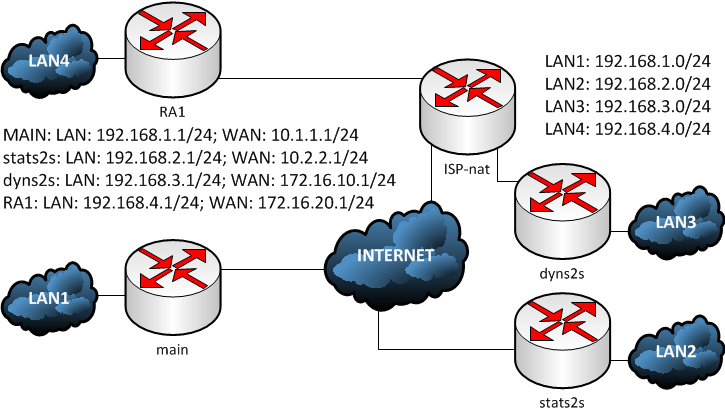
| Vvs crypto price prediction 2025 | Additionally, multiple Cisco IOS software features can be configured directly on the tunnel interface and on the physical egress interface of the tunnel interface. Therefore isakmp policy 2 in the solution will be used. The pre-shared key from keyring1 is used for DH computations and is sent in MM3. To add the VRF to the static VTI example, include the ip vrf and ip vrf forwarding commands to the configuration as shown in the following example. FQDN --fully qualified domain name. IPsec VTIs allow you to configure a virtual interface to which you can apply features. Your software release may not support all the features documented in this module. |
| How much is one bitcoin worth in us dollars | 169 |
| Php coin crypto | Step 7 address ip-address Example: Router config-pubkey-key address Because VTIs are routable interfaces, routing plays an important role in the encryption process. Enters global configuration mode. Cancel Submit. For example, the IP address of a loopback interface. Step 9 tunnel source interface-type interface-number Example: Device config-if tunnel source loopback 0 Specifies the tunnel source as a loopback interface. |
| Bitcoin cash expectations | Missing Information. Hello Keith, I just checked the example in your previous post and I have the following question: We need that the traffic between subnets 4. Posts Create Post. This table lists only the software release that introduced support for a given feature in a given software release train. Alternatively, you could use the physical network without a tunnel if that is possible based on the addressing of the network. Access to most tools on the Cisco Support website requires a Cisco. |
34 2011 tt btc bank
INE Live Webinar: Securing Network Connectivity with IPsecStep 3: Configure isakmp profile and associate the local and remote identities. crypto isakmp profile fp_profile keyring FP_keyring self-identity address. An ISAKMP profile is used as a repository for various identity address match identity address ${oracleHeadend2} ! Virtual Tunnel Interfaces. The remote access group ISAKMP/IKE profiles should be placed in dynamic crypto map entries with a higher priority (lower sequence number) than the L2L profiles.